The Problem
When it comes to online learning some companies have it easier than others.While some can do this via plain PowerPoint Karaoke, others have to provide a complete infrastructure with different servers, services, specialized/expensive software packages and so on. Usually this is done via a separated learning environment (like a training-room within the companies facilities)
But if the trainees can not come to the training-labs (eg. because of COVID-19 isolation) then you have to bring this environment to them. voice and slides (or the screen of the presenter) can easily be achieved via
- MS-Teams or
- VNC with teamspeak.
- BigBlueButton
- a local jitsi installation
- etc.
If you want that your trainees can use your (already existing) training computers in your training rooms then one possibility can be to enable them to log in via RDP (the Windows remote desktop connection protocol) at the locally provided training machines in the lab.
Let assume the following setup:
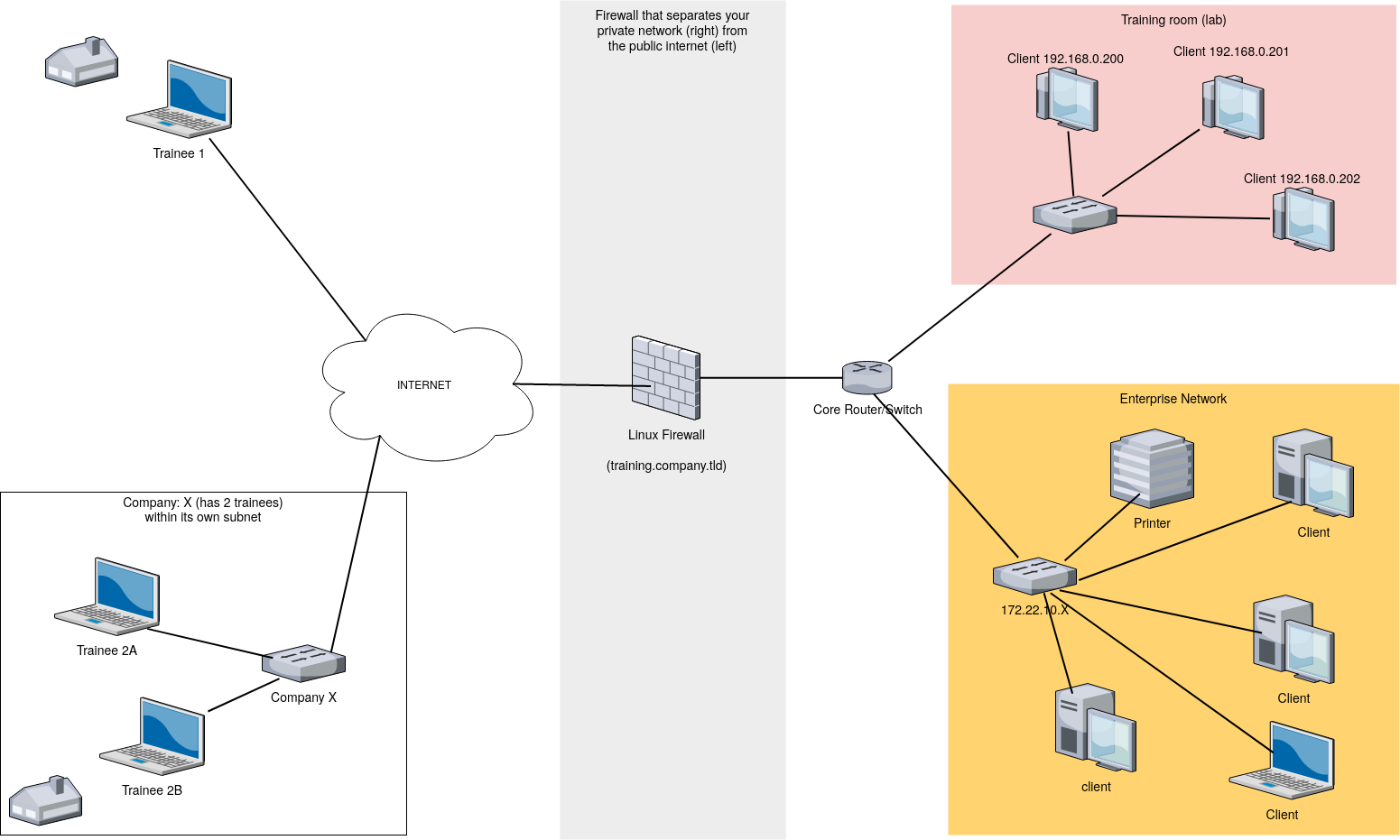
The trainees (on the left) want to access the training machines which are behind your firewall layer (gray) in the 192.168.0.X subnet (red box). Each trainee should have access to one training box.
The Solution
Assuming that neither the internal core switch, nor any traning-box does block any RDP traffic you have to configure your Linux firewall in a way where you create a 1:1 mapping from some random public ports to the port 3389 of your training machines.
Here are the commands that configure your linux iptables firewall to do so:
$sudo iptables -A FORWARD -p tcp --dport 5500 -j ACCEPT
$sudo iptables -A FORWARD -p tcp --dport 5501 -j ACCEPT
$sudo iptables -A FORWARD -p tcp --dport 5502 -j ACCEPT
# Enable Masquerade on the nat chain
$sudo iptables -t nat -A POSTROUTING -j MASQUERADE
# forward the requests to the training-boxes
$sudo iptables -t nat -A PREROUTING -p tcp --dport 5500 -j DNAT --to-destination 192.168.0.2oo:3389
$sudo iptables -t nat -A PREROUTING -p tcp --dport 5501 -j DNAT --to-destination 192.168.0.2o1:3389
$sudo iptables -t nat -A PREROUTING -p tcp --dport 5502 -j DNAT --to-destination 192.168.0.2o2:3389
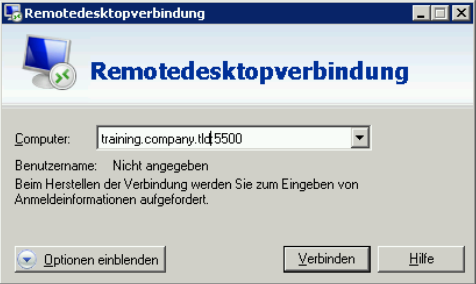
This creates the desired mapping. After that you have to tell your trainiees to connect to the desired port to be forwarded to the machine:
Thats it.