The Problem
Free wireless LAN is offered in every bigger building or company. The problem with these wireless LANs is that the internet can be they can be (and often is) somehow restricted. Sites could be blocked, services can be disabled and traffic can be sniffed easily with a simple off-the-shelf firewall. Fortunately there is a simple solution to this problem: Encrypt your traffic, route it to a secure destination and surf the web from there on.
This sounds complicated ? ... No - it isn't. Here is a simple solution utilizing a RaspberryPi (or any other Linux box which is under your control) as proxy server and a windows client with the right tools installed.
The Solution
As hinted in the previous paragraphs the solution is easy to build - if you know what you are doing. Since you are on this site I assume that you are not familiar with the necessary steps how to implement such an environment. So lets start with some explainations:
Proxy Server
A proxy server is a server is a server that accepts traffic and routes it to another destination. Technically you send ally your data packets to your proxy, which forwards the data to the desired destination. If he gets an answer then the proxy is going to return the answer to you.

Why would somebody like to do this ? ... Because the route to the destination can be blocked or restricted from your location. A famous example are restrictions based on your geolocation. Users from Europe are able to see content on youtube, where visitors from other continents may not. People who travel a lot may be aware of these issues. So if you manage to set up a proxy in a 'good' location then you can visit all sites that are visible from this location, because the proxy sends the requests to the desired server - and not you, sitting behind a restrictive firewall in your company.
Encryption
While the first problem (accessing sites from another location than yours) may be solved via a proxy server, we must not forget that we are facing another problem: Traffic that is routed through a proxy server can still be intercepted on your site - so we have to encrypt it. Encrypted data channels have a long history in computing. Nearly every Linux system offers a secure remote shell via SSH. The traffic to this shell is encrypted. No one (except a trojan horse on your computer or any other kind of locally installed malware) should be able to reconstruct the content of the data packets exchanged between you and the server running SSH.
Bringing all togehter
The good news is: SSH also offers a built in proxy. It is turned off by default, but it is really simple to turn it on. So lets start with the final requirements of our solution:
- Find a suitable or setup your own SSH Server and enable the proxy feature
- Connect to this server and route your traffic through it
In general every computer that runs Linux and which is under your control is a good candidate as proxy server. This can be a virtual server in a datacenter, a machine in your company DMZ or a small RaspberryPi. The keypoints are
- The machine must be accessible from everywhere. The location may be a factor if you try to circumvent geoiplocation based services. You can rent a virtual server with root access for a few bucks around every corner in the internet. Unfortunately a simple webspace is often not enough because you will not have access to modify the SSH configuration. A great option is a RaspberryPi which runs at home and which is accessible via a dynamic dns hostname (NoIp.org is a good candidate).
- SSH must be turned on, and the SSH configuration file /etc/ssh/sshd_config must have TCP Forwarding enabled. The line AllowTcpForwarding yes enables the feature. If it wasn't already enables append it to your configuration file and restart the SSH daemon.
Once you managed to setup the server you will need a client tool. Under linux you will need nothing, under Windows you can use PuTTY as client.
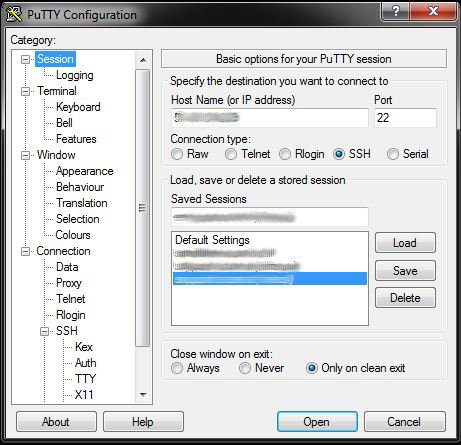
Putty is able to provide a local SOCKS Proxy (we will see how to use this later) that collects data and transmits it through the SSH tunnel. However: you have to tell PuTTY that you want to use this:
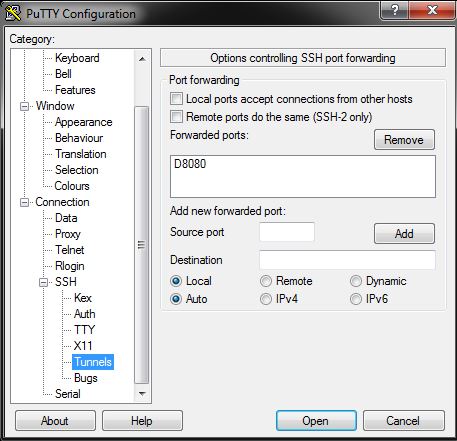
The important thing is to tell Putty to forward all ports. The list of forwarded ports has to contain the string "D8080". This parameter tells PuTTY to run a SOCKS5 server on the local machine on the port 8080. To bring the setting into the list do the following:
- Enter the value "8080" (without the D) in the box "source port"
- Tick the checkbox "Dynamic"
- Press the "Add" button
Finally save the settings and log into your proxymachine.
simpleuser@6.55.203.210's password:
Welcome to Ubuntu 14.04.2 LTS (GNU/Linux 3.13.0-55-generic x86_64)
* Documentation: https://help.ubuntu.com/
System information as of Mon Jul 6 12:28:19 CEST 2015
System load: 0.0 Processes: 89
Usage of /: 8.7% of 229.31GB Users logged in: 0
Memory usage: 8% IP address for eth0: 6.55.203.210
Swap usage: 0%
Graph this data and manage this system at:
https://landscape.canonical.com/
0 packages can be updated.
0 updates are security updates.
No mail.
Last login: Mon Jul 6 12:28:19 2015 from 5.33.76.122
simpleuser@proxymachine:~$ grep Forwarding /etc/ssh/sshd_config
X11Forwarding yes
AllowTcpForwarding yes
simpleuser@proxymachine:~$
The screenshot shows that I logged into my "proxymachine" with the user "simpleuser". The command grep Forwarding /etc/ssh/sshd_config is here to verify that AllowTcpForwarding is turned on. As long as you leave the PuTTY window open you will be able to send data encrypted to your proxymachine - as long as you tell your browser to do so.
However - once you are connected to the machine the browser has to know about the proxy. In firefox the proxy configuration looks like this:
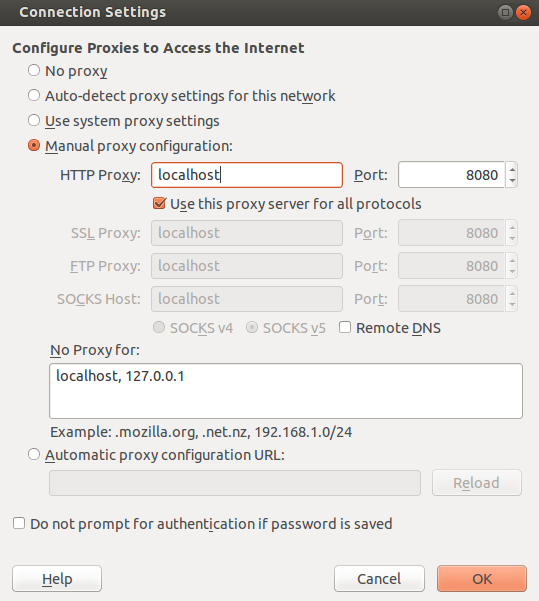
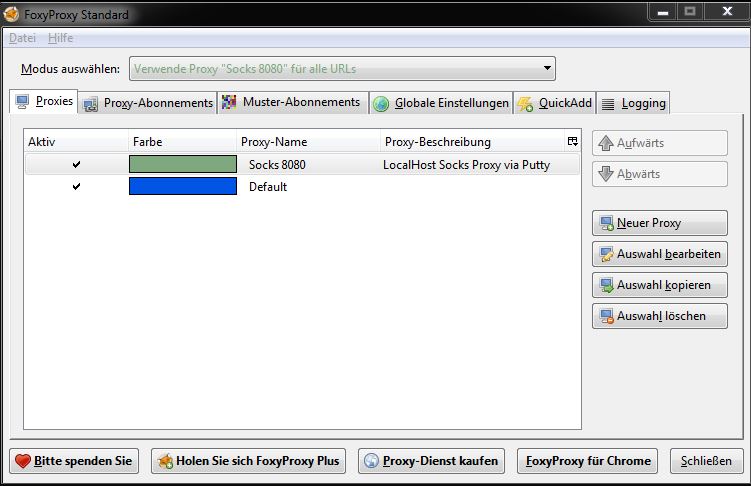
Another (more elegant) solution is to use the firefox extension FoxyProxy. This addon allows to switch on and off different proxies on the fly, by clicking a single button and even by matching addresses with regular expressions. If you are not allowed to install plugins the keep in mind that you can run firefox as portable application.
My setup looks like this:
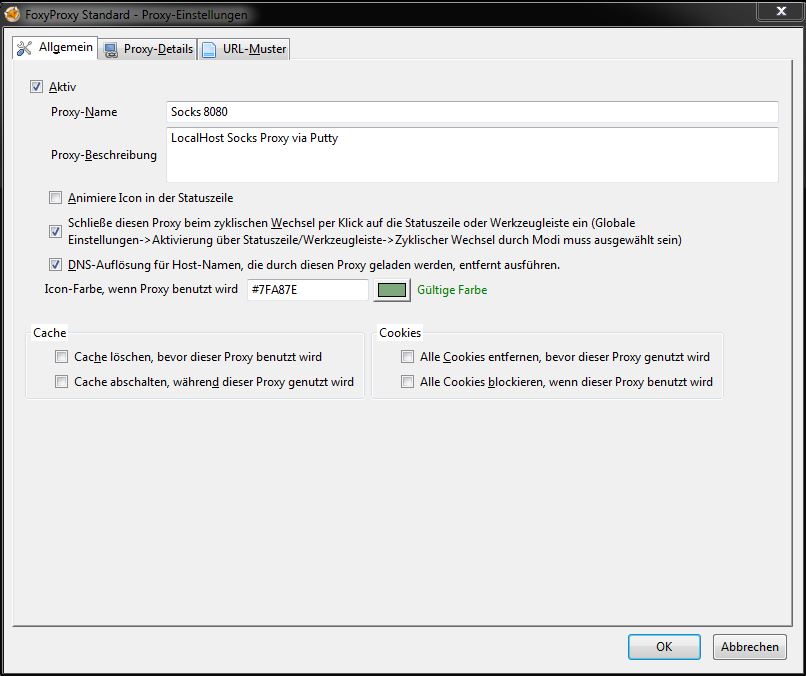
First I added a new proxyserver to the configuration.
The proxy is active ...
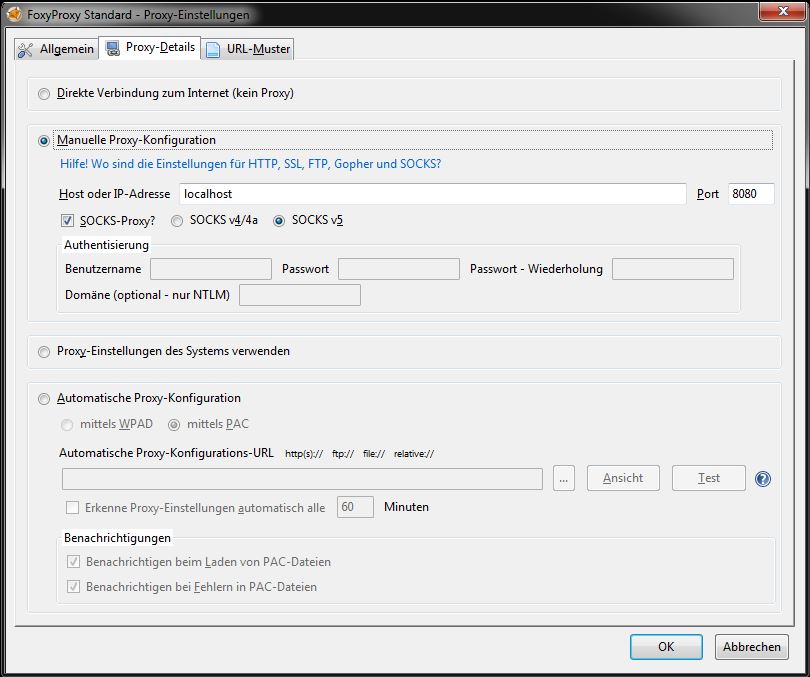
... and is a running SOCKS Proxy (provided by PuTTY) on the local machine on port 8080.
Finished. All requests from firefox are forwarded to PuTTY (which provides a SOCKS server on port 8080 or whatever port you choose in the forwarded ports dialog). This SOCKS proxy takes your data, transmits it via SSH to your proxymachine. The proxy machine is the exit of the encrypted tunnel. Responses to the site-requests are processed in reverse order.